Entra ID App Registration
3 minute read
Docusnap can automatically create an application in Azure AD for the inventory of Microsoft 365 and assign the required permissions (see chapter Create Azure Apps). Depending on the Azure policies in place in the environment, however, the automatic creation of the application or the automatic assignment of individual permissions may be blocked. In these cases, manual creation and configuration of the application in the Azure portal is required.
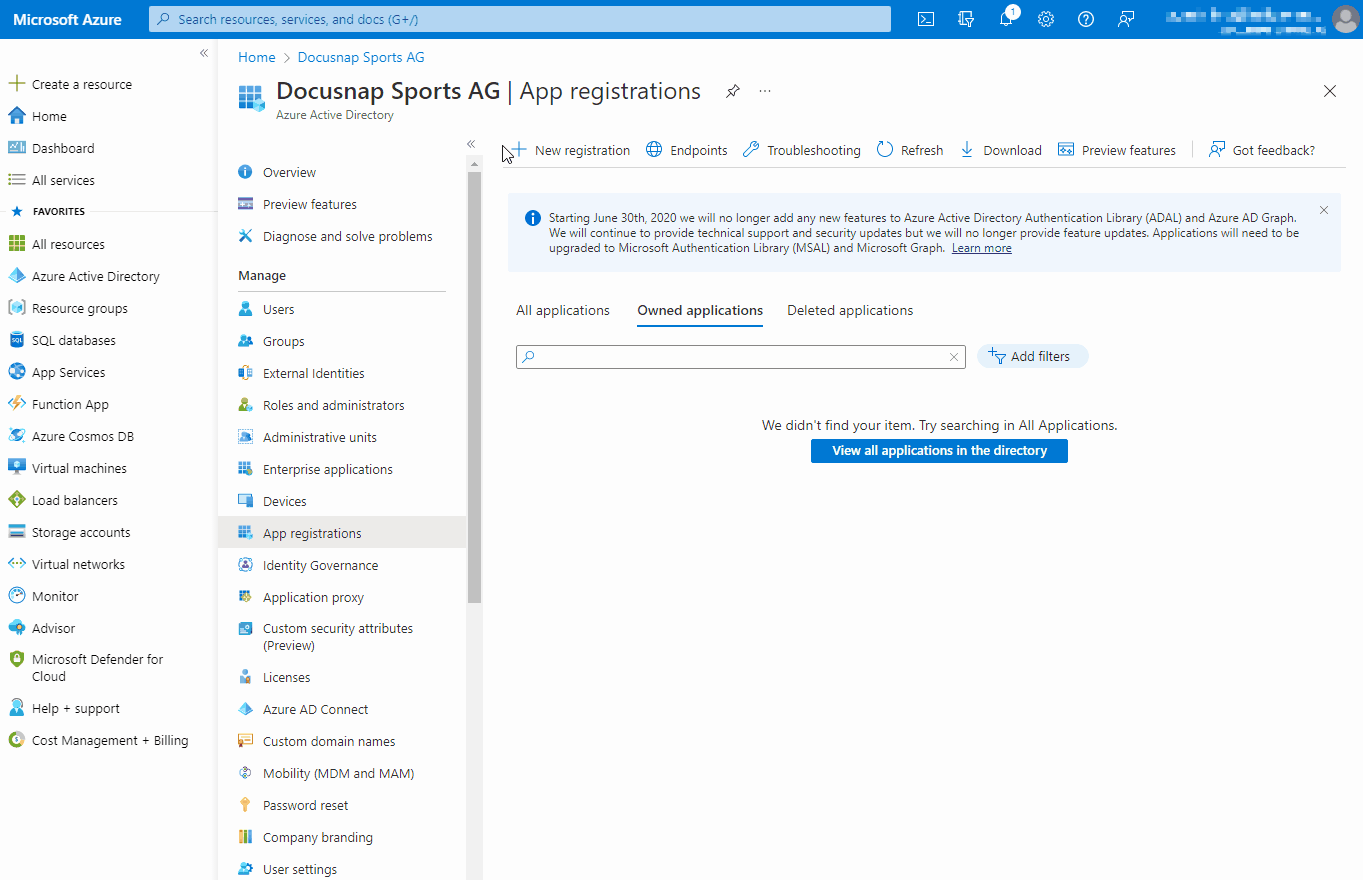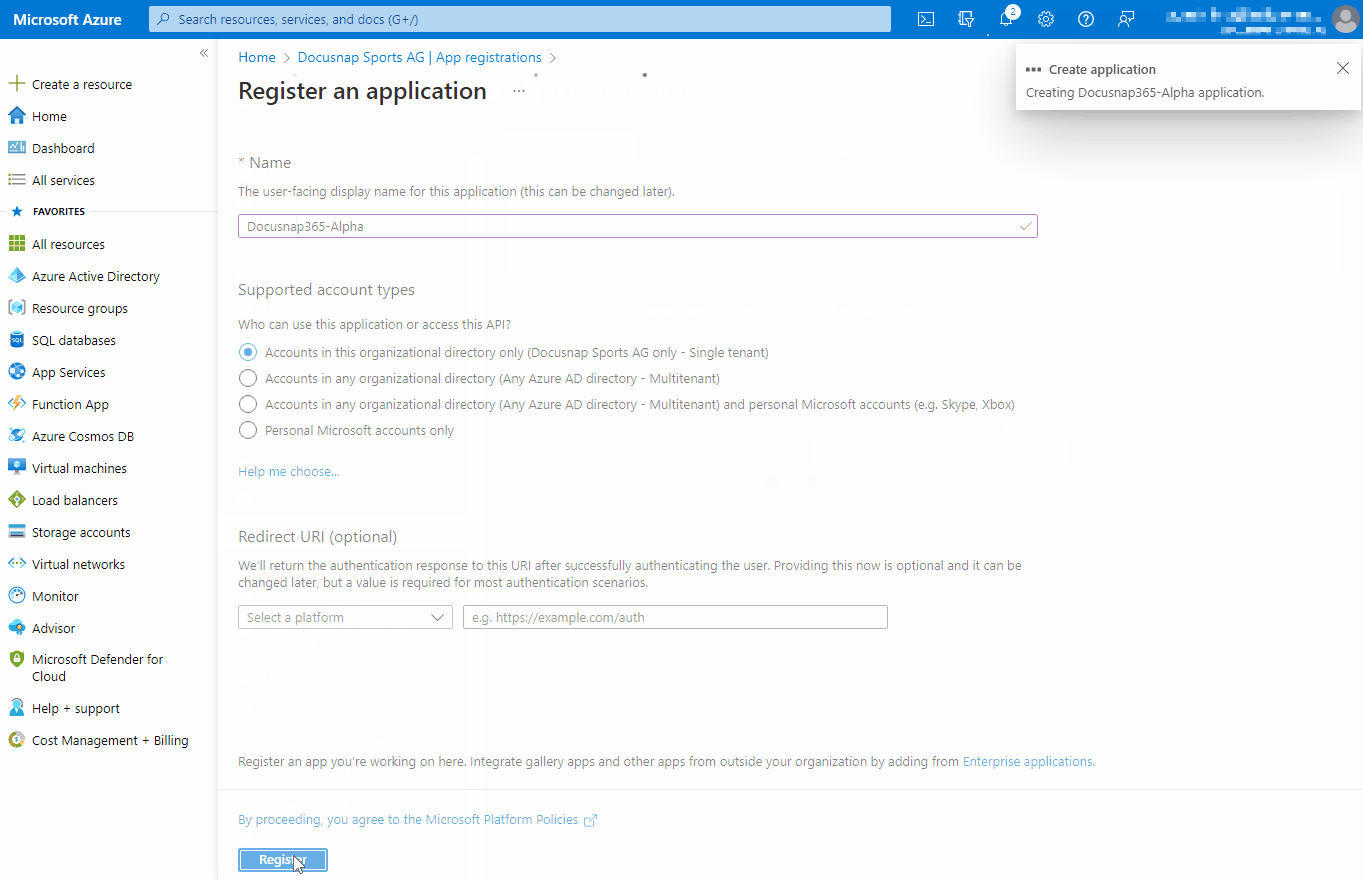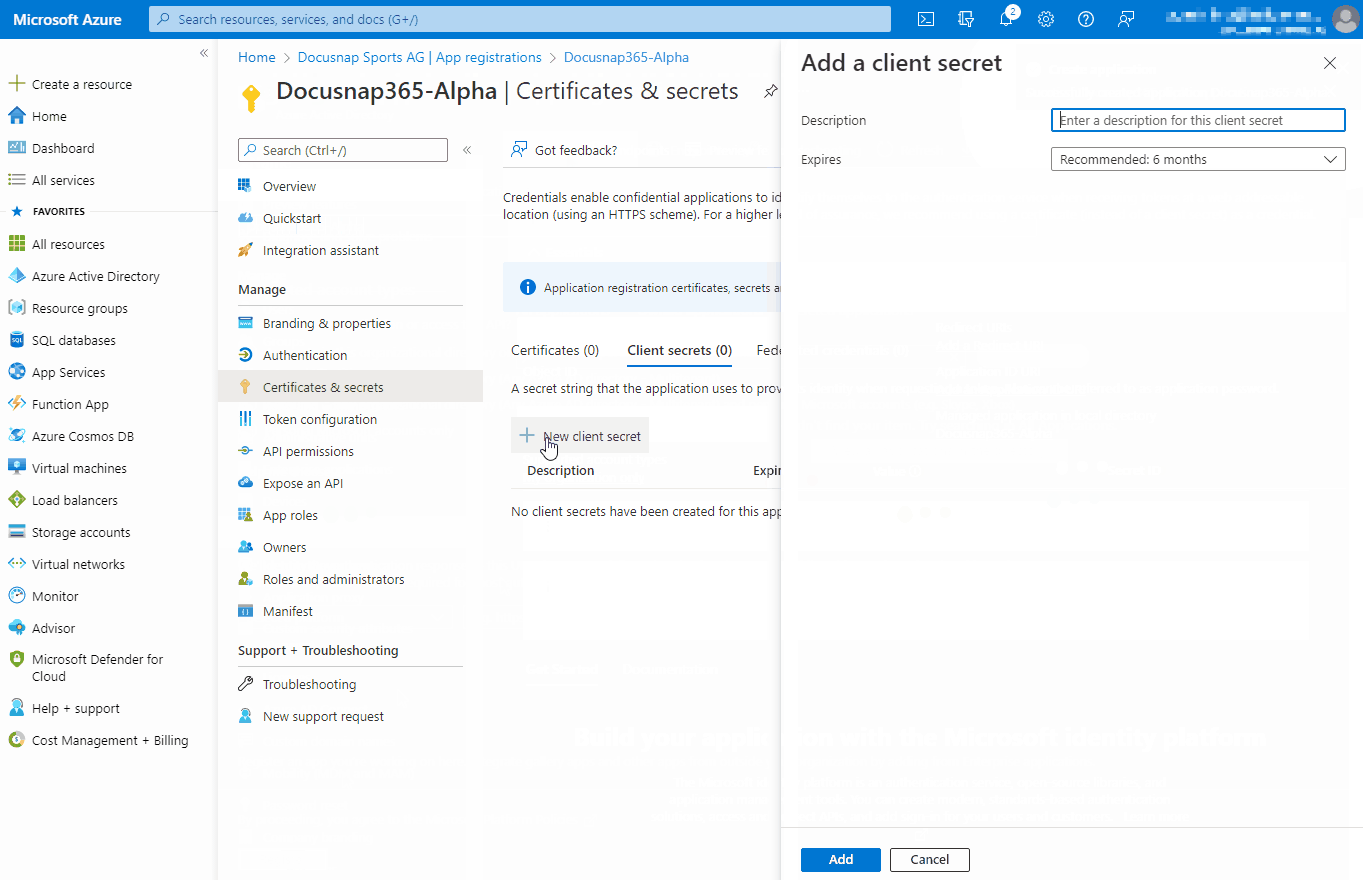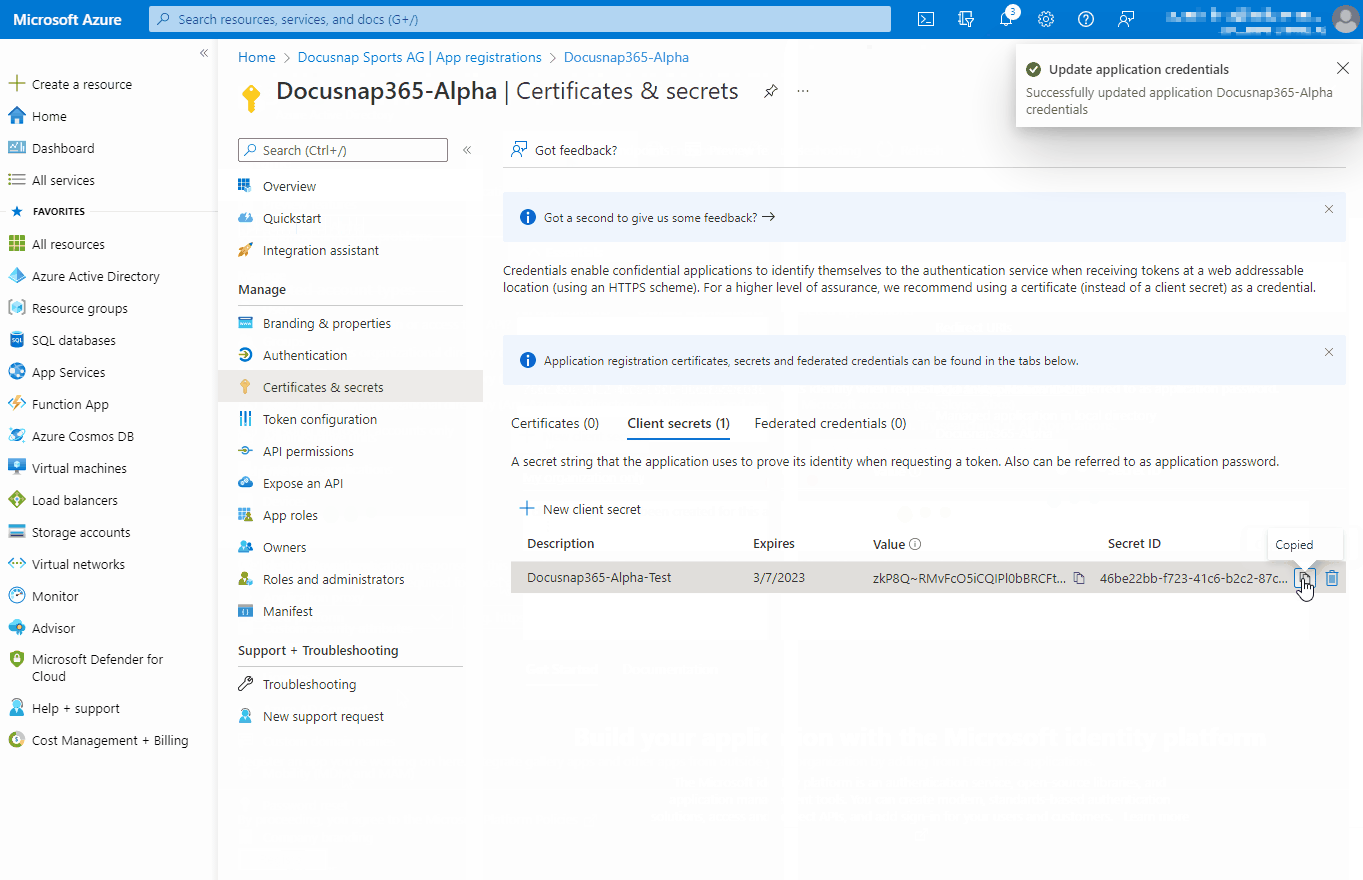
The registration of an application is done via the Azure Portal (portal.azure.com), in the Microsoft Entra ID section under the menu item “App Registration”.
Registering an application
API Permissions
To access a protected resource such as Teams information or SharePoint web pages, Docusnap365 needs authorization from the resource owner. Docusnap365 needs read-only access for Microsoft 365 discovery.
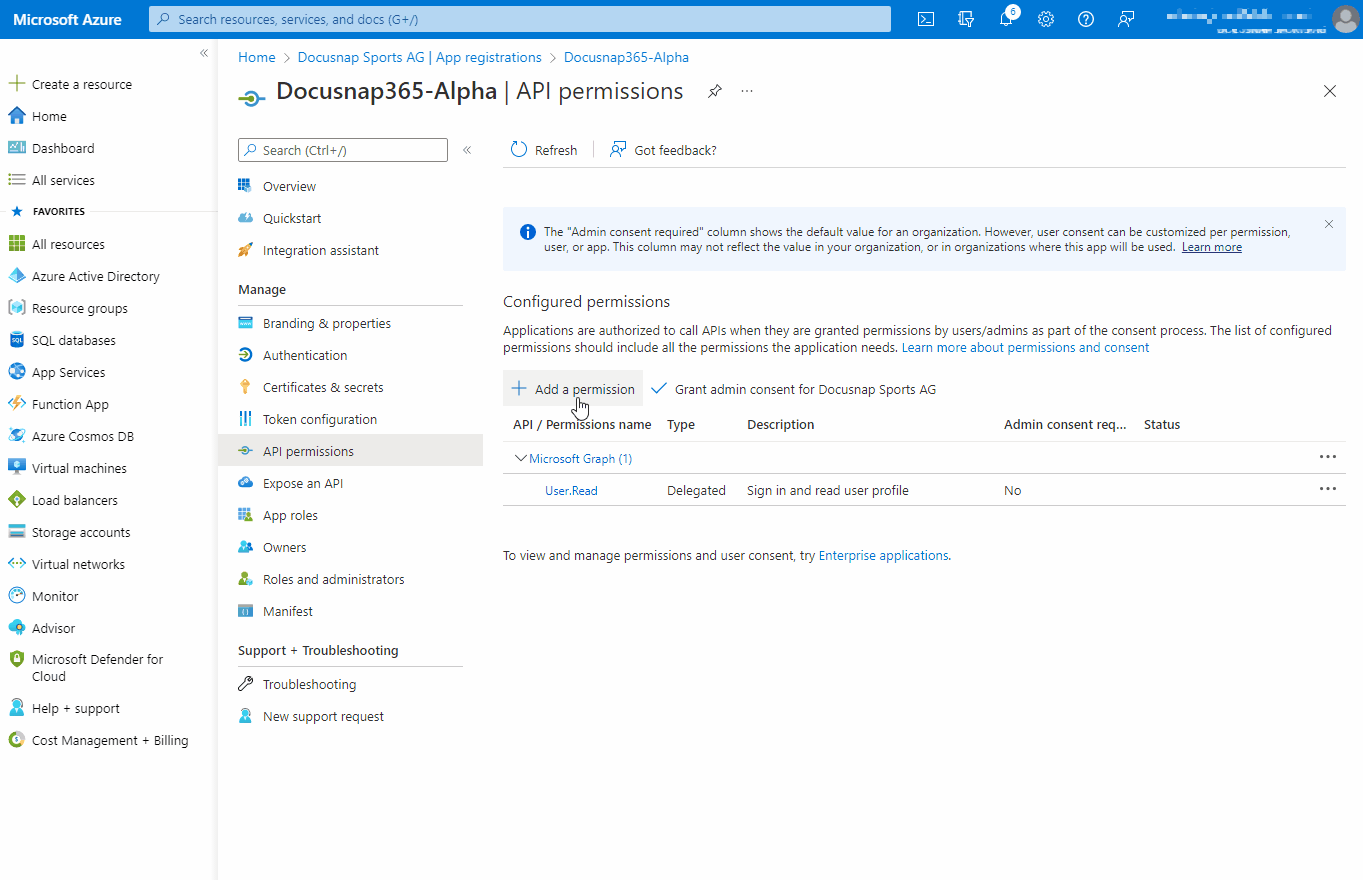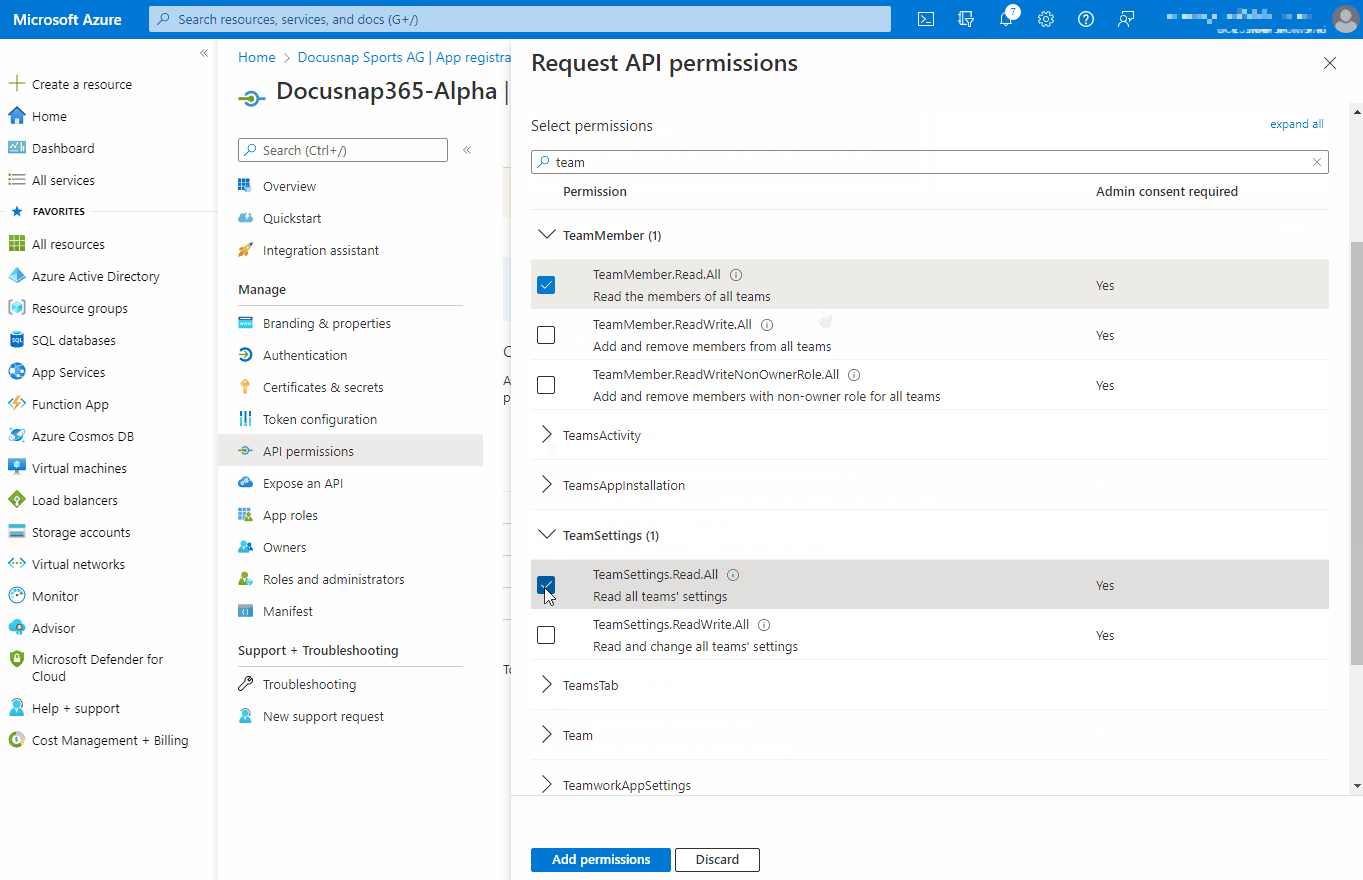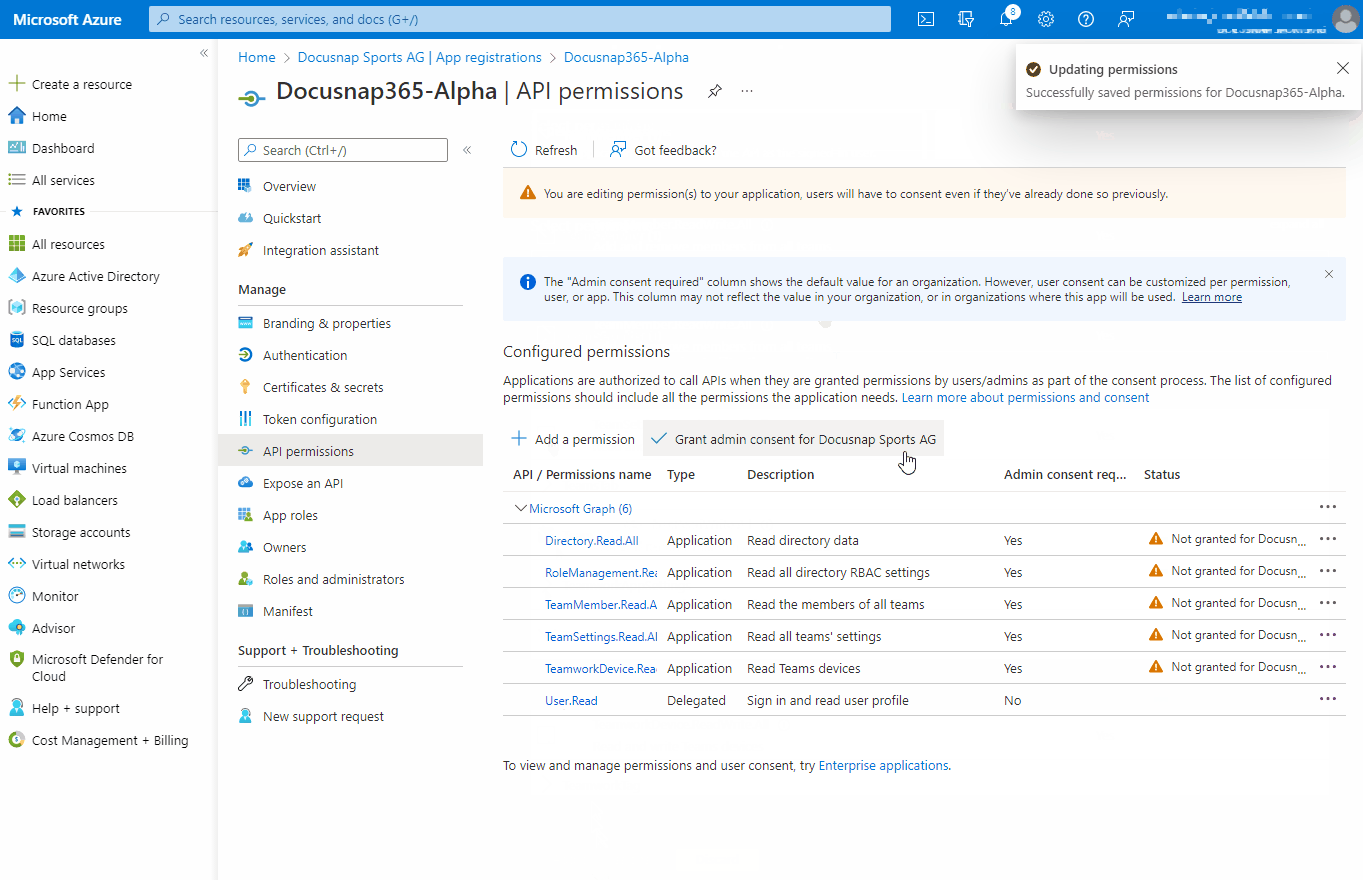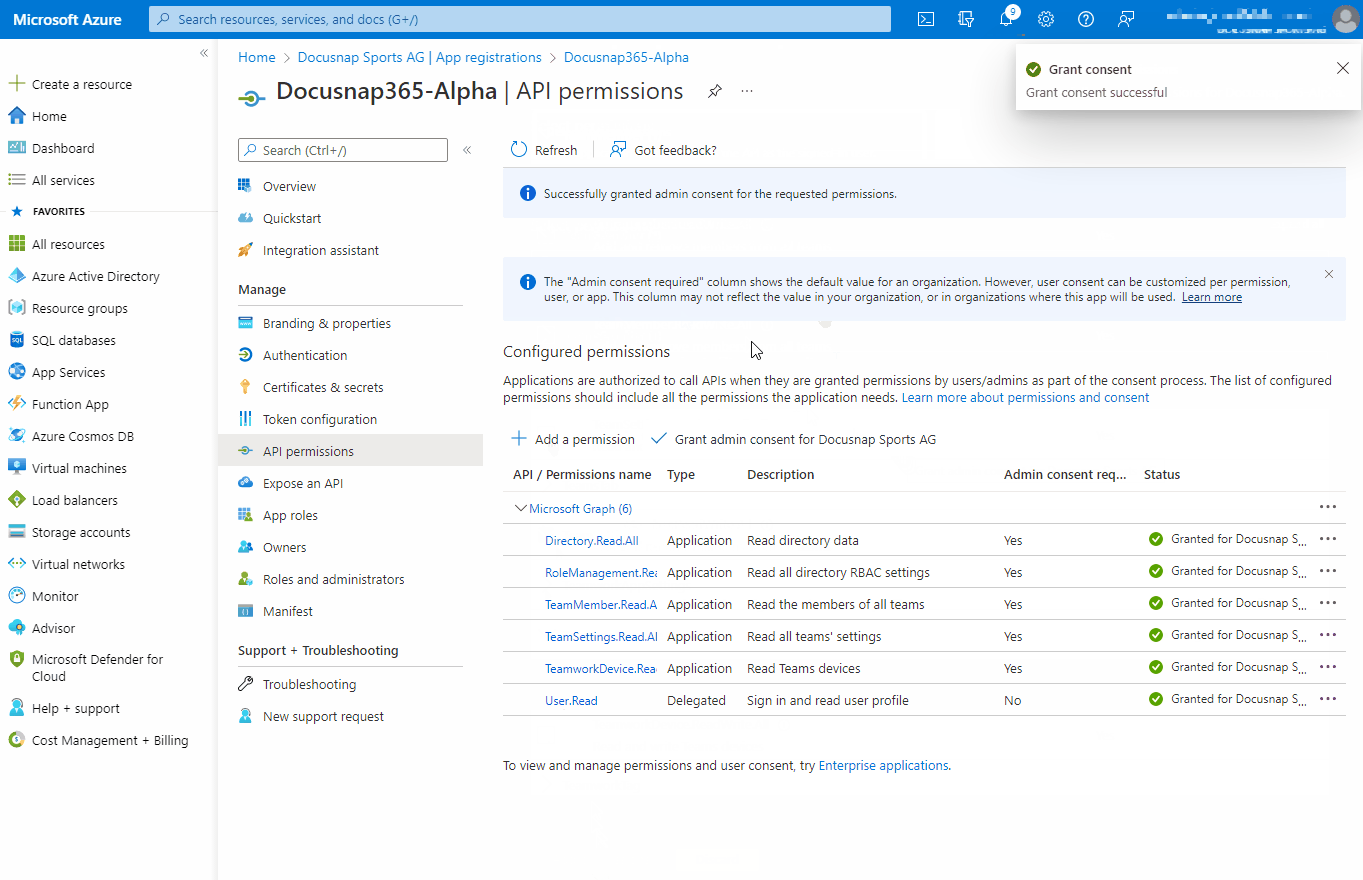
| API/Permission Name | Type | Description |
|---|---|---|
| AppCatalog.Read.All | Application | Read all app catalogs |
| Application.Read.All | Application | Read all applications |
| AuditLog.Read.All | Application | Read all audit log data |
| Calendars.Read | Application | Read calendars in all mailboxes |
| Channel.ReadBasic.All | Application | Read the names and descriptions of all channels |
| ChannelMember.Read.All | Application | Read the members of all channels |
| ChannelSettings.Read.All | Application | Read the names, descriptions, and settings of all channels |
| Contacts.Read | Application | Read contacts in all mailboxes |
| Device.Read.All | Application | Read all devices |
| Directory.Read.All | Application | Read directory data |
| Files.Read.All | Application | Read files in all site collections |
| GroupMember.Read.All | Application | Read all group memberships |
| Mail.ReadBasic | Application | Read basic mail in all mailboxes |
| MailboxSettings.Read | Application | Read all user mailbox settings |
| Organization.Read.All | Application | Read organization information |
| Policy.Read.All | Application | Read your organization’s policies |
| Reports.Read.All | Application | Read all usage reports |
| RoleManagement.Read.Directory | Application | Read all directory RBAC settings |
| SharePointTenantSettings.Read.All | Application | Read SharePoint and OneDrive tenant settings |
| Sites.FullControl.All | Application | Have full control of all site collections |
| Sites.Read.All | Application | Read items in all site collections |
| Team.ReadBasic.All | Application | Get a list of all teams |
| TeamMember.Read.All | Application | Read the members of all teams |
| TeamSettings.Read.All | Application | Read all teams settings |
| TeamsTab.Read.All | Application | Read tabs in Microsoft Teams |
| TeamworkDevice.Read.All | Application | Read Teams devices |
| TeamworkTag.Read.All | Application | Read tags in Teams |
| User.Read | Delegated | Sign in and read user profile |
| User.Read.All | Application | Read all users full profiles |
| UserAuthenticationMethod.Read.All | Application | Read all users authentication methods |
“Send As” (M365 Exchange Online)
When Microsoft 365 is inventoried, all mailbox permissions in Exchange Online are correctly detected by Docusnap without requiring additional role assignments. An exception is the “Send As” permission.
This permission is managed exclusively in Exchange Online and can only be retrieved if the application used in the Entra ID app registration is assigned the optional RBAC role Exchange Recipient Administrator.
Since this is an administrative role that does not follow the principle of least privilege, it is not assigned during automatic app creation. The assignment must therefore be performed manually in the Microsoft Entra admin center.
Assignment in the Microsoft Entra admin center
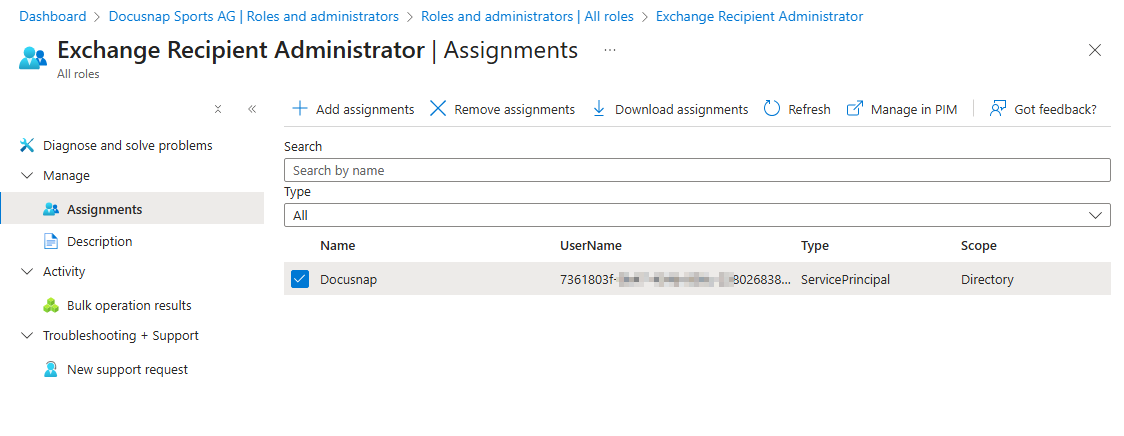
- Open Entra ID → Roles & administrators.
- Select Exchange Recipient Administrator.
- Choose Assignments → Add assignments.
- In the selection dialog, choose Service principals and mark the app used by Docusnap.
- Confirm with Add.
- Under Assignments, verify that the app is now listed.