IT Security
3 minute read
The IT Security ribbon is displayed when switching to IT Security in the navigation area.
NTFS Analysis: Click the NTFS Analysis button to open the wizard to select the Windows systems whose permissions are to be inventoried.
Online Analysis: The permissions will be determined at runtime by the Online Analysis process and thus not stored in the database. The Online Analysis process will be active once you click the Online Analysis button.
Filter Path: The Filter Path dialog only opens for the analysis of SharePoint permissions. Since the SharePoint permission structure is different from the structure of NTFS permissions, this dialog is used to select the desired starting point for the analysis. According to the filter you set, only the directories below the starting node that correspond to the selected users/groups will be displayed.
Report Jobs (csv): By importing a CSV file multiple jobs to generate Directory Reports for NTFS can be created simultaneously.
Clicking the NTFS Filter option opens the Manage NTFS Filter dialog. In this dialog, you can specify directories to be excluded from the NTFS analysis. For an explanation of this dialog, refer to the NTFS Filter section.
You can use the User/Group Filter to exclude selected users and groups from the directory reports.
Blocked Inheritance: Inheritance can be blocked for directories. This means that the permissions will not be inherited. If the Blocked Inheritance checkbox is enabled, the directories for which inheritance is blocked will be displayed with a red icon in the Permission Analysis explorer.
Special Permissions: If this checkbox is enabled, special permissions will be displayed in addition to the basic permissions.
Explicit Permissions: Permissions can be assigned directly to directories. If the Explicit Permissions checkbox is enabled, all directories to which permissions have been assigned explicitly will be displayed with a blue icon.
Additional functions are available in the action bar.
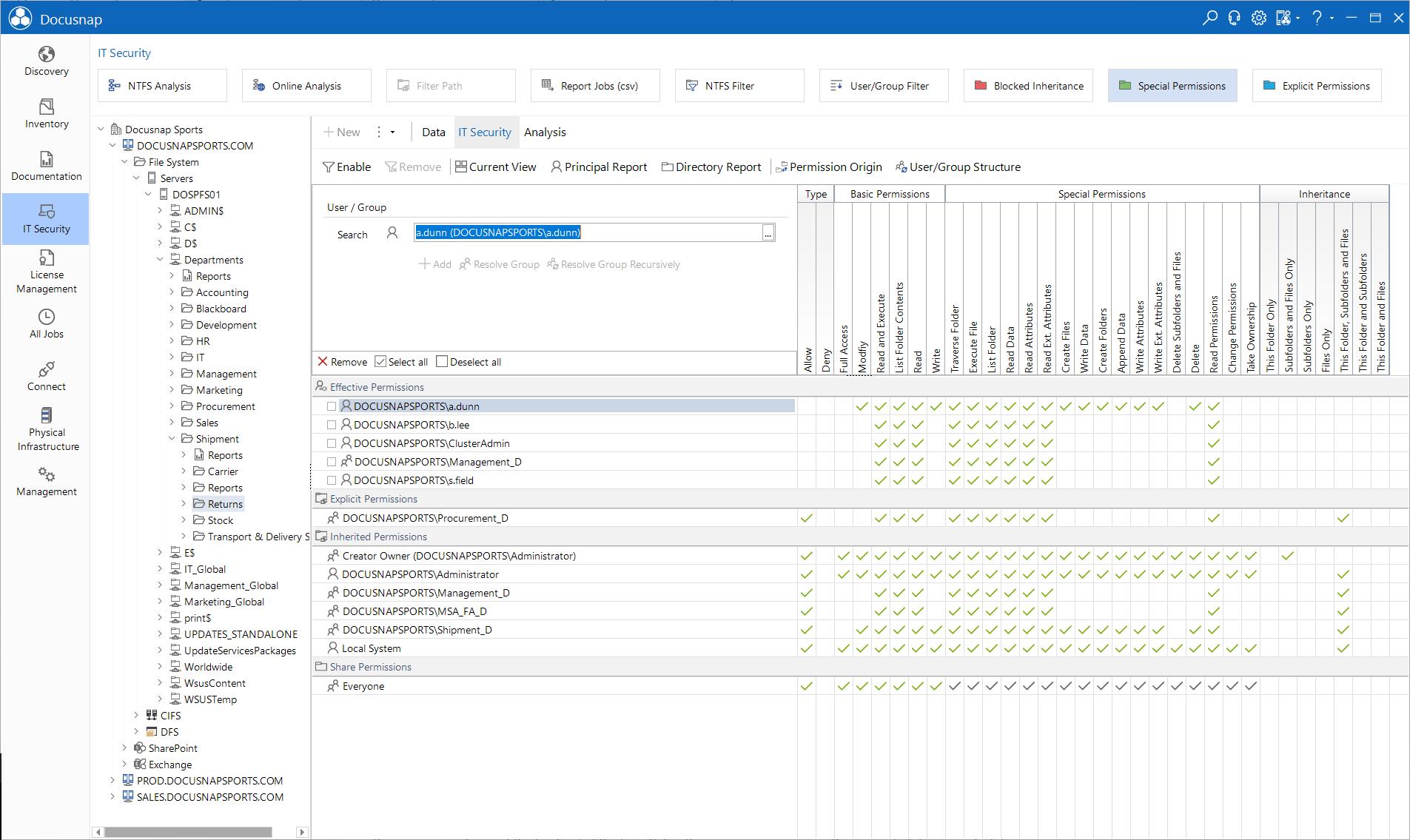
Enable/Remove: The Data Explorer displays all directories of a scanned system. To display the filter below the permissions list, click the Enable button in the Filter group of the ribbon. Once you have defined the desired filter criteria (Write, Read, etc.), only those directories will be displayed in the Data Explorer that match the selected user or group filter.
When you click the Current View button, the permissions displayed on the Permission Analysis tab will be output in a report.
By clicking the Principal Report button, you can create a report which shows the effective permissions to the selected directory and its subdirectories or for Exchange permissions to the mailboxes, mailbox folders, and public folders.
Clicking the Directory Report button creates a report which displays all users who have a permission to the selected directory and its subdirectories.
Permission Origin: Click the Permission Origin button to open the permission structure for the currently selected user.
User/Group Structure: Click the User/Group Structure button to display the group or user nestings diagram.
Clicking the Overview Report button creates a report which displays all users who have permissions to the mailboxes, mailbox folders, and public folders.
The IT Security explorer displays the shares that were determined by inventorying the Windows system. After a permission analysis, the tree view reflects the directory structure of the share.
Below the SharePoint and Exchange headings, the IT Security data explorer displays the SharePoint and Exchange permissions and offers them for analysis.
For more information on this topic, refer to the IT Security chapter.
The company is shown at the top level of the tree. Below the company, you can see the associated domains which have been inventoried. Below each domain, you can find the File System, SharePoint, and Exchange nodes where the corresponding permissions are listed.
When you select a directory in the Explorer, the main window displays the IT Security tab that includes information on share permissions, inherited permissions, explicit permissions, and the resulting effective permissions.